We’ve noted in previous CSC studies[1],[2],[3] that phishing continues to be an extremely popular threat vector with bad actors and shows no signs of subsiding—in part, because of the COVID-19 pandemic and the rise in popularity of remote working. Indeed, the most recent figures from the Anti-Phishing Working Group (APWG)[4],[5] show that the numbers of phishing attacks are higher than ever before, with the quarterly total of identified unique phishing attacks exceeding 1 million for the first time in Q1 2022, and over 600 distinct brands attacked each month.
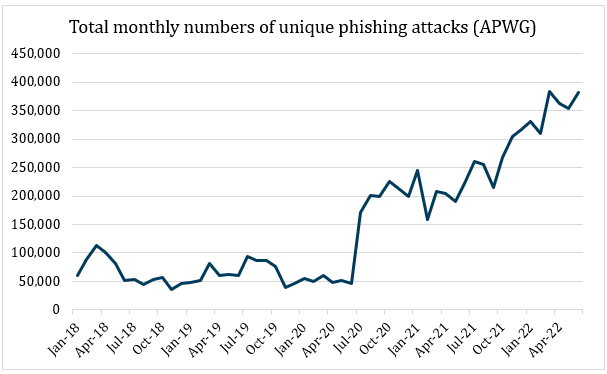
An earlier report by APWG[7] noted that over 80% of phishing sites were found to be employing secure socket layers (SSL) or transport layer security (TLS) certificates (allowing use of HTTPS)—an increase from around 5% at the end of 2016—and 90% of these certificates had been issued by free providers, such as cPanel and Let’s Encrypt.
Furthermore, Interisle’s 2022 Phishing Landscape study[8],[9] reported the detection of over 1.1 million phishing attacks between April 2021 and April 2022, with over 2,000 brands targeted, but the majority targeting just 10 top brands. Overall, 69% of attacks made use of specifically registered domains, with the attacks disproportionately concentrated on new generic top-level domains (gTLDs). Additionally, a small number of registrars dominate the malicious registrations. Around 41% of domains reported for phishing were found to have been used within 14 days of their registration, and most of these were reported within 48 hours.
Modern phishing is driven by the desire for credential theft and business impersonation, but it’s also increasingly recognized as the gateway for launching malware and ransomware attacks, which often lead to serious compromises of corporate systems and other security issues, such as domain name system (DNS) attacks.
The customizable phishing site
Central to many phishing attacks is the use of a fraudulent look-alike site mimicking the appearance of the official site of the brand being targeted—often including a login form prompting the input of sensitive customer information which thereby falls into the hands of the fraudster. In a classic phishing attack, the site will impersonate a specific brand, and cybercriminals will send emails to a wide group of users driving them to the site. This strategy uses the assumption that a certain portion of the recipients will be genuine customers of the targeted brand and may be fooled.
However, over the last two years, CSC has noted the emergence of a much more egregious style of phishing site, the appearance of which is dynamically tailored to the specific recipient in each case and can successfully target a much broader portion of recipients from a single campaign.
An example was first identified in February 2020, using a URL of the form https://[fraudsite.com]/[directory]/?usr=[string], where “string” was a series of apparently random characters. The site appeared to target the user of a specific corporate email address relating to a brand owner, with the address pre-populated into the login form on the page. The background of the site displayed a framed version of the official company website, giving the appearance that the user was logging into their own corporate site. All of this content appeared to be hard coded into the HTML of the phishing site.
However, closer inspection revealed that the content actually appeared to be dynamically generated, with the string in the URL comprising a Base64-encoded version (a standard method of converting binary data, such as a string of standard ASCII characters, into an alternative text format) of the recipient email address.
To determine how the phishing site handled this information in practice, a modified URL was generated, replacing the previous Base64 string with an encoded version of a CSC employee email address. This produced the page shown in Figure 2, for which the HTML source code again appeared to be hard coded when viewed.

The implication is that the site is presumably running a script to dynamically generate the HTML of the page, based on the content of the Base64 string within the URL. This provides the potential to generate a very convincing, customized phishing attack whereby, given a recipient email address, the fraudulent site is configured to display a framed version of the host domain of the email address, overlain by a login box pre-populated with that address. Consequently, the same phishing email could potentially be sent to large numbers of email addresses, with no further requirement to customize the email or the corresponding phishing site to the recipients in question—beyond ensuring that a Base64-encoded version of the recipient email address is appended to the link in the phishing email in each case (which could easily be automated via use of a script).
It was also established that the behavior of the site appears to be dependent on exactly how and where it’s viewed, with the site appearing inactive when viewed in a virtual machine environment. This type of configuration has previously been noted as a technique used by fraudsters to thwart forensic analysis of their sites by security professionals, who often work in virtual environments.
It’s also notable that this type of site would be very difficult to detect using traditional brand monitoring approaches. Aside from the fact that the site may have been set up as an unindexed island site, intended to be accessed only via links in spam emails, there’s potentially no reference to any brand in the site content itself, with brand-specific content being generated dynamically in the HTML only when a specific URL is accessed. In this type of case, detection would be dependent on the ability of CSC’s anti-fraud engine, working in conjunction with web referrer information provided by the brand owner, to identify when the phishing site draws information from the brand owner’s official site when the framing process is carried out.
A study in July 2022[10],[11] reported the identification of an extremely similar style of attack, in this case using a bit-for-bit mirror of the official site of the brand being targeted.
Conclusions
These findings highlight the importance of a comprehensive phishing detection and enforcement program, able to identify threats of a variety of types. Detection should incorporate domain monitoring (to identify phishing sites where the brand name—or a variant—is included in the domain name) and internet monitoring (to identify other fraudulent sites linked from content indexed by search engines) components. However, other data sources—such as spam traps and honeypots, and other data feeds like customer abuse mailbox data and webserver logs—should also be used to identify phishing sites that are unindexed or feature content that is more dynamically generated.
However, even this is only part of the solution. As noted above, phishing attacks often form the basis for subsequent malware attacks or other security incursions. Accordingly, a robust security posture should also include the deployment of a range of domain security measures—such as those offered by an enterprise-class registrar—to protect critical corporate domains. It’s also advisable for brand owners to avoid the use of service providers who allow unsavory practices such as typosquatting, domain name auctions, and name spinning (the sale of domains containing brand variations)—all of which can facilitate phishing attacks.
If you’d like to find out more about phishing detection, visit our enterprise fraud solutions page or complete our contact form to speak with one of our experts.
[1] cscdbs.com/blog/branded-domains-are-the-focal-point-of-many-phishing-attacks/
[2] worldtrademarkreview.com/global-guide/anti-counterfeiting-and-online-brand-enforcement/2022/article/going-phishing-countering-fraudulent-campaigns
[3] cscdbs.com/blog/going-phishing-countering-fraudulent-campaigns-2/
[4] docs.apwg.org/reports/apwg_trends_report_q1_2022.pdf
[5] docs.apwg.org/reports/apwg_trends_report_q2_2022.pdf
[7] docs.apwg.org/reports/apwg_trends_report_q2_2021.pdf
[8] interisle.net/PhishingLandscape2022.html
[9] interisle.net/PhishingLandscape2022.pdf
[10] darkreading.com/endpoint/apt-phishing-mirrors-landing-pages-credential-harvesting
[11] avanan.com/blog/mirroring-actual-landing-pages-for-convincing-credential-harvesting
