
By Vin D’Angelo, Quinn Taggart, and Sue Watts Share this post 


In light of the Biden administration’s recent efforts in protecting critical infrastructure from cyber threats, new research from CSC indicates that a majority of the top energy companies* in the U.S. are vulnerable to attack due to shortcomings in their online operations. Specifically, these organizations are vulnerable to domain name and domain name system (DNS) hijacking and phishing attacks based on their lack of effective domain security.
Highlights of CSC’s research on these top energy companies indicates:
| Nearly 80% are not using registry locks | 67% are registered with consumer-grade domain registrars (vs enterprise-grade registrars) | Only 17% use DNS hosting redundancy | Only 3% use DNS security extensions (DNSSEC) | 73% of companies use Domain-based message authentication, reporting, and conformance (DMARC) |
This analysis was conducted on the 30 largest US companies by market capitalization that produce and deliver energy in the US. With that being said, the findings are consistent with the domain security posture of 90+ global “energy” companies that are part of CSC’s Forbes Global 2000 report.
Each of the security measures listed above are industry best practices that help mitigate against cyber attacks, and they’re part of CSC’s defense in depth approach. Threats of not deploying these security measures include:
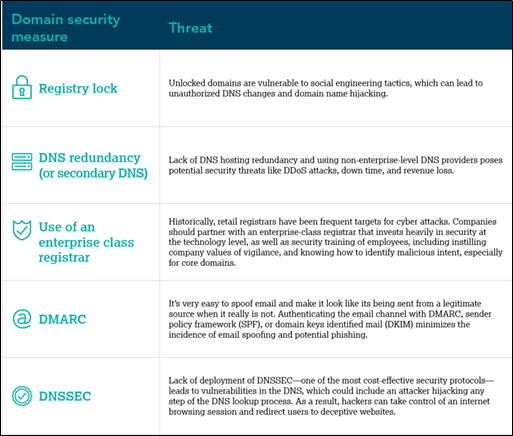
At CSC, we talk about locking your vital domains as being your first—and best—line of defense. Only 17% of these utility companies are leveraging tools like a registry lock, which leaves the rest vulnerable to social engineering, unauthorized DNS changes, and domain name hijacking.
In addition, 67% of these companies are relying on consumer-quality practices for securing their web domains, which puts them at exponential risk for some of today’s most common cyber threats. Companies need to understand how their choice of provider fits into decisions made about their organization’s overall cyber security posture, along with concerns about IP infringement and trademark law. When it comes to the domain ecosystem, choice of domain registrar can affect colleagues responsible for cyber security and IT, as well as legal (general counsel), risk, and compliance (chief risk officer)—because it has a major impact on cyber security, phishing attacks and online fraud, and brand abuse.
To manage a domain name portfolio, company’s need to work with a provider that has invested in protecting its own systems. With all of the cyber security threats today, not only does a good domain name registrar need to have the right technology—to protect itself and client companies from a data breach—but it also needs best-in-class operations practices that put security at the forefront of its mission, and in how it engages with its clients.
An enterprise-level registrar should have ISO 27001 accredited data centers, SOC 2® compliance, third-party penetration and vulnerability testing. They should conduct regular security tests, including SQL injection and cross-site scripting (XSS). They should also be Internet Corporation for Assigned Names and Number (ICANN) and country-code top-level domain (cctld) registry accredited. A registrar that’s qualified to serve an enterprise will offer a full accounting of all domains, DNS, and digital certificate providers. It should provide 24/7/365 support along with cyber security training for its staff, including phishing and social engineering awareness. It’s also important for an enterprise-class registrar to:
- Mandate written requests (never via phone)
- Be data and General Data Protection Regulation compliant (e.g., WHOIS practices)
- Have a registry transfer-lock policy
Looking at CSC’s research, only 17% of the energy companies have DNS hosting redundancy, and the lack of this security measure makes them more susceptible to DNS vulnerabilities or a costly distributed denial of service (DDoS) attack. DNSSEC is another proven mitigation tool for DNS threats, as it protects organizations from cache poisoning, but it also has very low use at just 3%. DMARC use is optimistically high, and with the growth and damage done by phishing attacks today, this is a good sign. As the Biden administration takes a closer look at the security around major utilities, it’s imperative that these organizations reassess their approaches to securing their domain security ecosystem to follow enterprise-class strategies for more effective security. All of these security measures will have an immediate effect on cyber risk at these energy companies, and will help mitigate the prospect of attacks that can lead to network breaches, system outages, and nefarious actions by bad actors.