Introduction
Domain tasting is a long-established practice involving the short-lived existence of a domain, which is allowed to lapse a few days after its initial registration. The practice arose in response to an Internet Corporation for Assigned Names and Numbers (ICANN) policy allowing a domain to be cancelled—with all fees refunded—within a five-day grace period, intended to address the issue of accidental registrations[1]. However, the practice is open to abuse by infringers.
Historically, domain tasting was frequently used for determining the amount of web traffic received[2]. Large numbers of domains could be speculatively registered and monetized through the placement of pay-per-click (PPC) links. The domains could also be used for sending spam emails, for example. At the end of the grace period, those receiving significant amounts of web traffic could be retained for further use, or sold at a profit, with the others being allowed to drop.
However, numerous previous studies have also established that many domains used for phishing are also only active for a short period of time—potentially as part of a means of evading detection and takedown[3]—whether being dropped inside the formal five-day grace period or after it.
In this study, we consider short-lived domains with names targeting any of the top 10 most valuable brands in 2022[4],[5], and look at patterns and trends in these registrations. This analysis follows on from CSC’s general observation of the threats posed by branded domain names is of central importance in cybersecurity initiatives[6].
Methodology and findings
CSC used the domain monitoring component of its 3D Domain Security and Enforcement technology to consider registration activity events (new registrations (N), re-registrations (R) or domain drops (lapses) (D)) for domains with names containing any of the top 10 global brand names—including variants such as fuzzy matches and homoglyph matches—over a one-month period across September and October 2022.
In this study, we define a domain tasting event as an instance of a specific domain name being both registered (N or R) and then subsequently dropped (D) within that one-month period. It’s important to note that this will include both true tasting events (where the domain is allowed to lapse within the five-day ICANN grace period) and other instances of short-lived domains. These might include examples where a domain is dropped by its owner—potentially outside the grace period—after a period of use (say, for launching a phishing attack) or taken down by a brand owner or service provider following identification of an infringement.
Across the 10 brands, 1,753 domain tasting events were identified within the one-month period, with the breakdown by brand shown in Figure 1. Within the dataset, six individual domain names were tasted twice within the monitoring period.
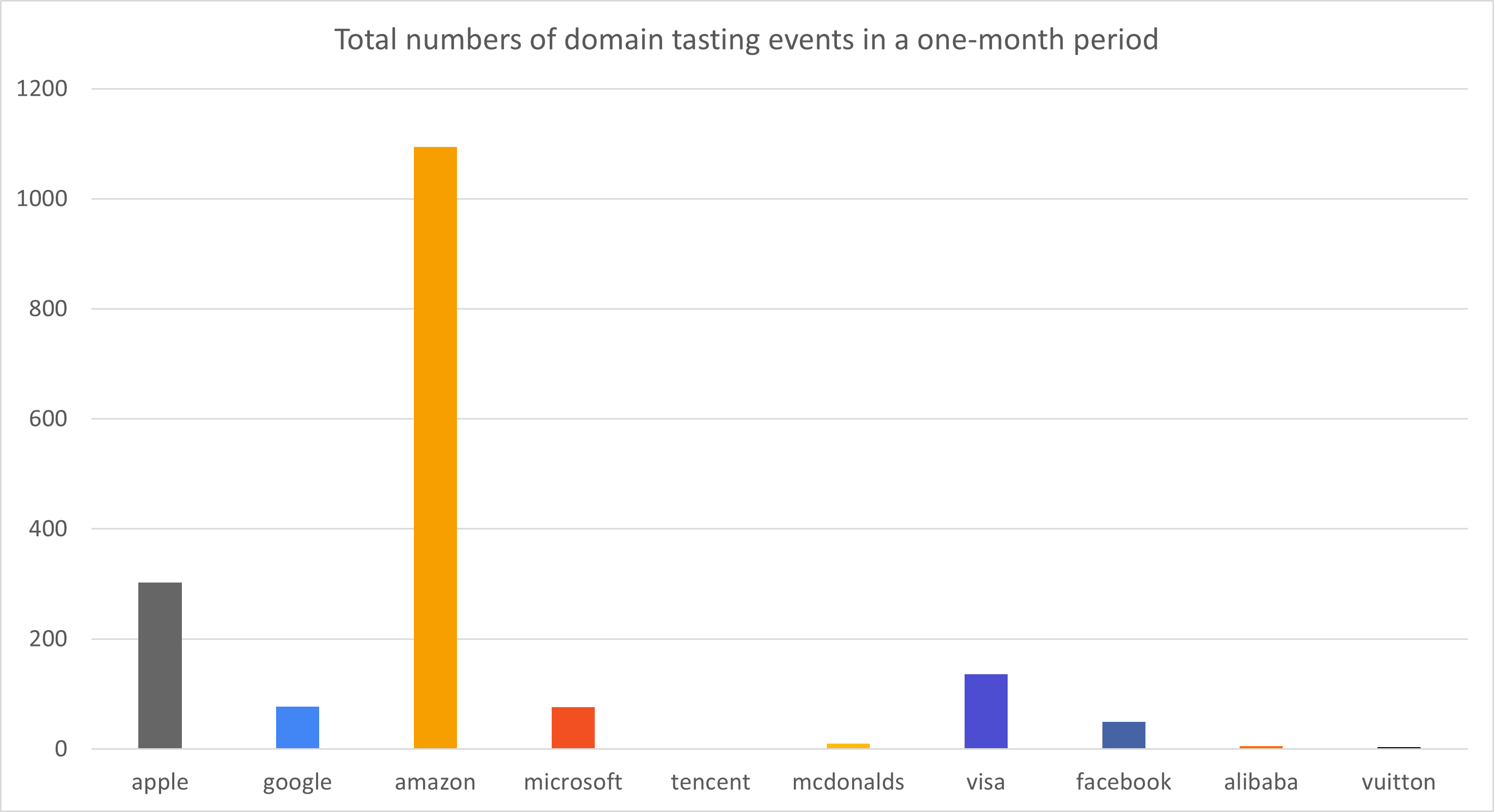
Figure 2 shows the daily total numbers of observed tasting events for each brand.
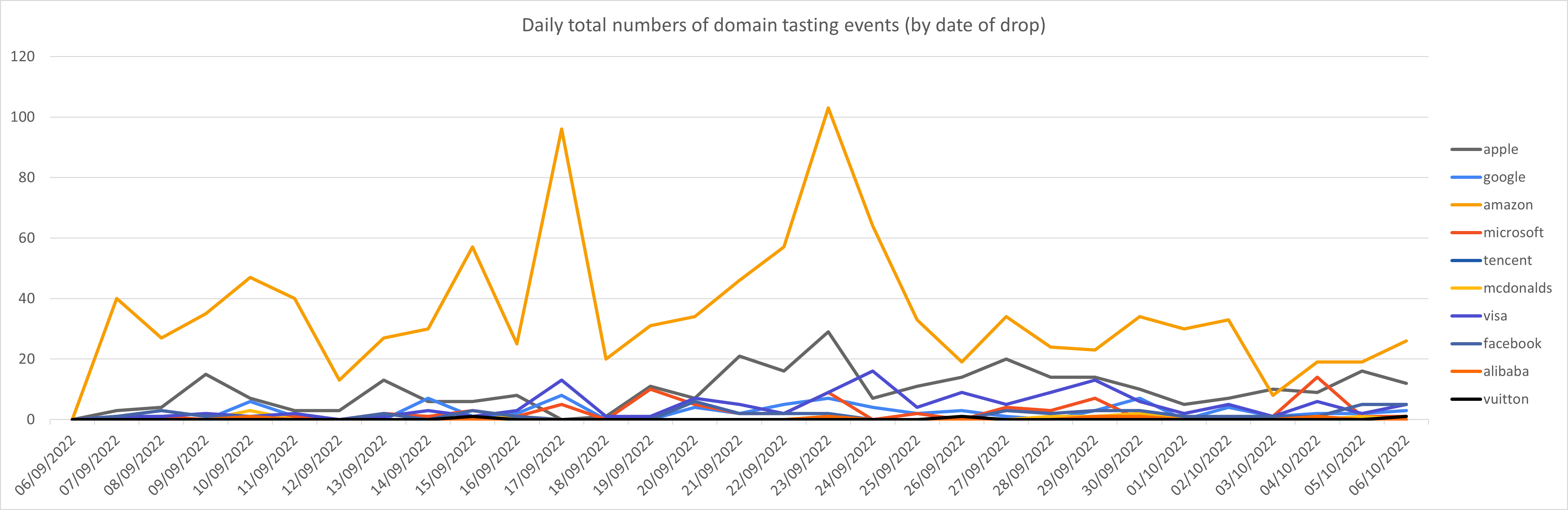
Figure 3 shows the total numbers of domain tasting events, categorized by the delay between registration and drop. The vast majority of the tasted domains (1,469 out of the 1,753, or 83.8%) were live for five days or less, consistent with the ICANN grace period, although several were active for somewhat longer, with the longest observed delay between registration and drop in the dataset being 28 days (for one example). Across all observed tasting events, the average (mean) delay was 3.70 days.
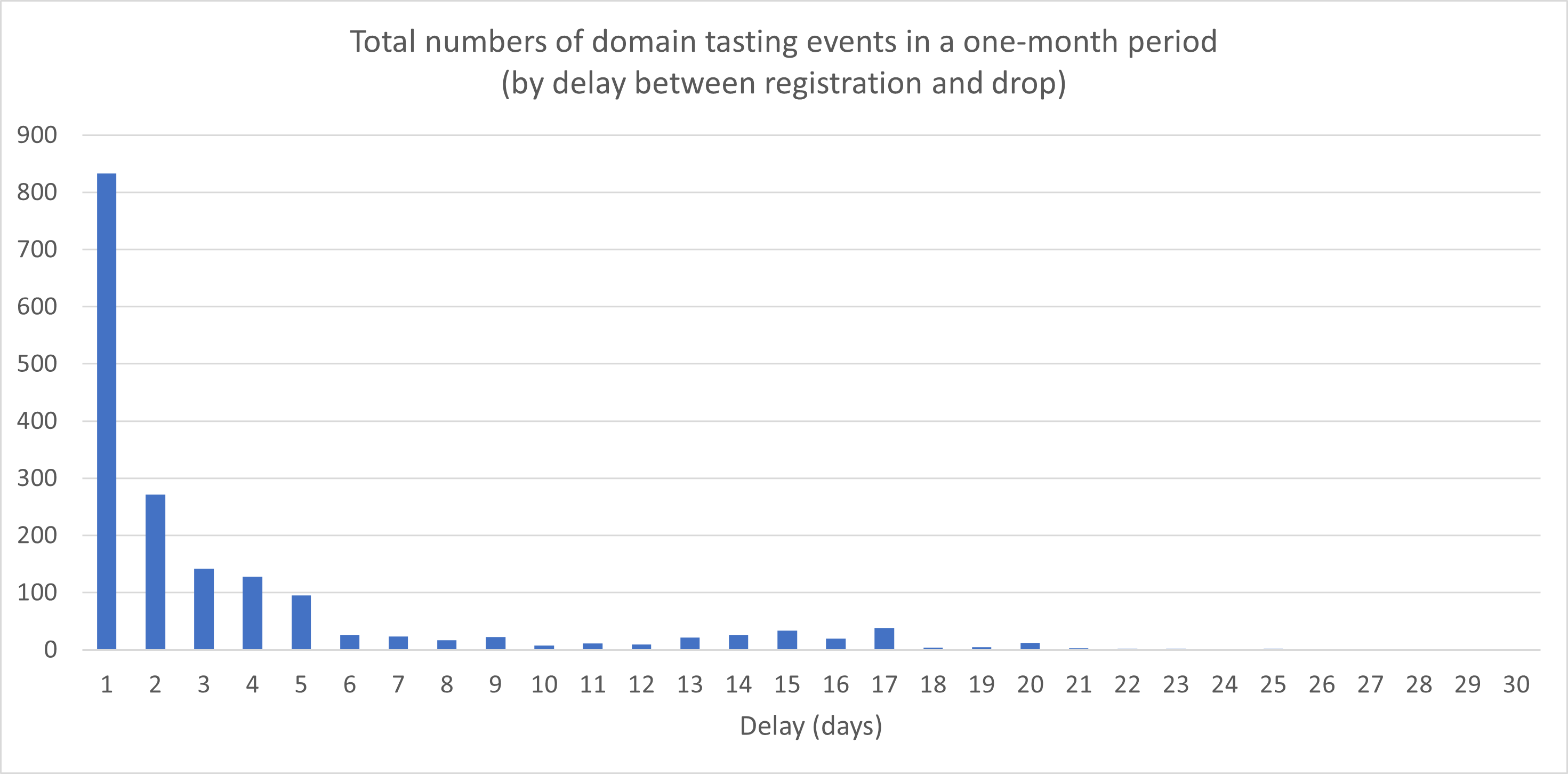
Table 1 shows the top-level domains (TLDs) or top domain extensions represented in the dataset. The most popular extension was .COM by a significant margin, though a number of new generic TLDs (gTLDs) were also popular. These extensions have been previously noted as being popular with infringers[7],[8],[9].
| TLD | No. domains | % domains |
| .com | 1,301 | 74.22% |
| .online | 61 | 3.48% |
| .info | 40 | 2.28% |
| .shop | 38 | 2.17% |
| .org | 36 | 2.05% |
| .xyz | 23 | 1.31% |
| .co.uk | 22 | 1.25% |
| .top | 21 | 1.20% |
| .site | 21 | 1.20% |
| .store | 18 | 1.03% |
| .net | 16 | 0.91% |
| .link | 15 | 0.86% |
| .vip | 15 | 0.86% |
| .support | 12 | 0.68% |
| .website | 11 | 0.63% |
| .live | 11 | 0.63% |
It’s also informative to consider the frequently-occurring keywords present in the tasted domains alongside the targeted brand names. Figure 4 shows a selection of the most popular keywords, and indicates that many of these are either: (i) keywords frequently associated with phishing-related content (e.g., verif-, account, login or secur-); or (ii) generic popular keywords that might be expected to attract significant volumes of search-based web traffic (such as support, online, service, help, apps, shop, and store).
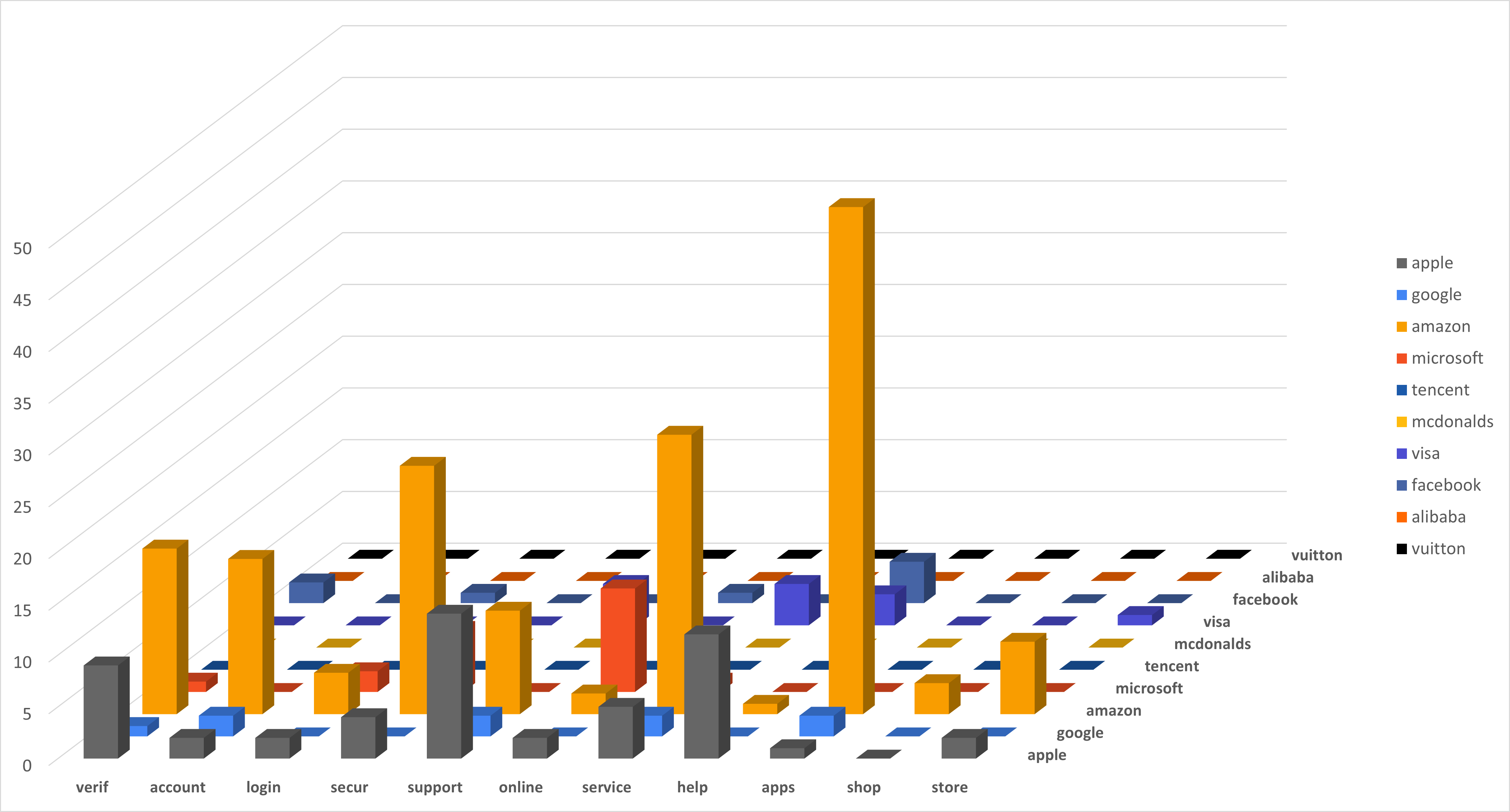
From this analysis, a variety of specific patterns can be identified. For example, keywords such as “service” and “help” appear commonly in tasted domains in conjunction with the brands Apple®, Amazon® and Visa®, while phishing-related keywords are frequently associated with Apple, Amazon, Microsoft®, and Facebook®. Other observed trends were less predictable, such as the large numbers of Amazon-related “apps” domains. The majority of these are domains of the form apps-amazon-XXXYYY.com or apps-XXX-amazonYYY.com, where XXX is an additional keyword (such as billing, payment, service, or support) and YYY is a string of digits. Domains with consistent name structures of this type can be used for a variety of purposes—either infringing or legitimate—including phishing activity, as part of the build process for new websites, or for security or penetration-testing audits.
Discussion
One aspect of domain tasting which may be particularly attractive to fraudsters is the ability to register large numbers of similar domain names, at low (or no) cost. This strategy provides the potential to effectively hide the much smaller subset of domain names that may be intended to be weaponized for, possibly, phishing activity. Additionally, the observation of the drop activity for those domain names that are not used can also provide a false sense of security to the brand owner. Furthermore, other attack types such as spam and malware distribution, and the construction of botnets for attacking infrastructure, can also benefit from bulk registration of domains[10].
Overall, these observations highlight the importance of brand owners proactively monitoring domain registration activity by third parties. CSC’s 3D Domain Security and Enforcement technology provides an effective overview of such activity, including the ability to look at brand variations, generate data on the time interval between domain registrations, drops, and re-registrations (thereby giving insight into tasting events), and provide details on the associated keywords used in the domain registrations. This information can yield valuable guidance on the highest risk domain-name structures, keywords and TLDs, which can help drive an informed policy on defensive registrations. A defensive strategy will, however, only take a brand owner so far, because of the infinite permutations of brand terms and keywords that can be used by bad actors[11]. It’s for this reason that a defensive domain registration program should always be accompanied by a domain and brand monitoring program to track ongoing activity by third parties outside the firewall.
[1] en.wikipedia.org/wiki/Domain_tasting
[2] techopedia.com/definition/15657/domain-tasting
[3] worldtrademarkreview.com/article/energy-crisis-related-scams-highlight-how-bad-actors-seek-capitalise-global-events
[4] en.wikipedia.org/wiki/List_of_most_valuable_brands
[5] kantar.com/inspiration/brands/what-are-the-most-valuable-global-brands-in-2022; the brand terms used in our analysis are: Apple; Google; Amazon; Microsoft; Tencent; McDonalds; Visa; Facebook; Alibaba; and Vuitton.
[6] Holistic brand, fraud and cyber protection using domain threat intelligence
[7] cscdbs.com/blog/branded-domains-are-the-focal-point-of-many-phishing-attacks/
[9] CSC Analysis of Threatening Domains Targeting the Top 10 Most Valuable Brands
[10] interisle.net/sub/CriminalDomainAbuse.pdf
[11] worldtrademarkreview.com/global-guide/anti-counterfeiting-and-online-brand-enforcement/2022/article/creating-cost-effective-domain-name-watching-program
