by Ken Linscott
In the first post in this series, we covered what DNS is, why it’s important, and how it works. Today, we turn our attention to four ways DNS is vulnerable to attack.
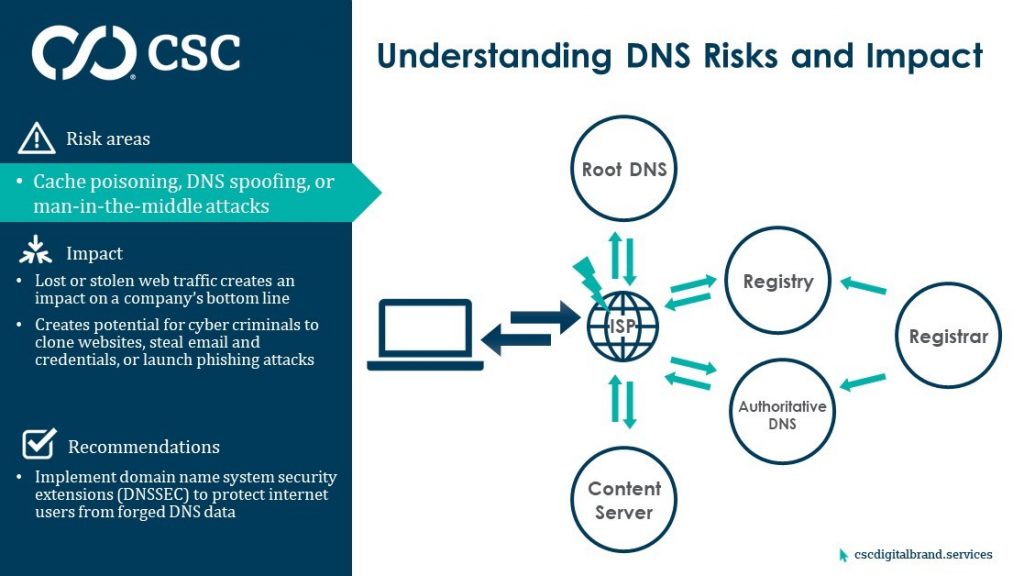
1. DNS cache poisoning
Internet queries first go to the internet service provider (ISP), and if the ISP has the IP address saved (cached), the computer resolves to the right web location.
Herein lies the first potential threat of DNS cache poisoning. If the ISP has been compromised, cyber criminals can replace the cached IP address with a fraudulent website they control, re-routing a company’s web traffic to content of their choice.
2. Poor domain name management
If the ISP doesn’t have the IP address cached, it will query the root DNS to ask it which registry to visit for the authoritative content. It’s at this registry level where companies are exposed to further risk and the next threat.
There’s a risk that poor domain management has led to the domain registration lapsing, meaning that website no longer exists, so the registry is not able to respond.
- Failure to renew important domains is surprisingly more common than most companies think, and in most cases is due to a poor choice of registrar or not understanding the crucial role of domains in an organization’s structure.
- Website visitors will have a poor experience, and any other service within a business that’s being supported by the lapsed domain will no longer function—most notably email, which also the most important yet unofficial company workflow tool.
The threat is that expired domains could be available for registration by others, including cyber criminals who can easily direct visitors to a spoofed website and start using the domain to launch phishing attacks against a company’s clients. And just because a domain registration has lapsed does not mean access to that specific company has been erased. Inbound emails from clients and staff of the former domain owner can be intercepted and harvested by bad actors for confidential information.
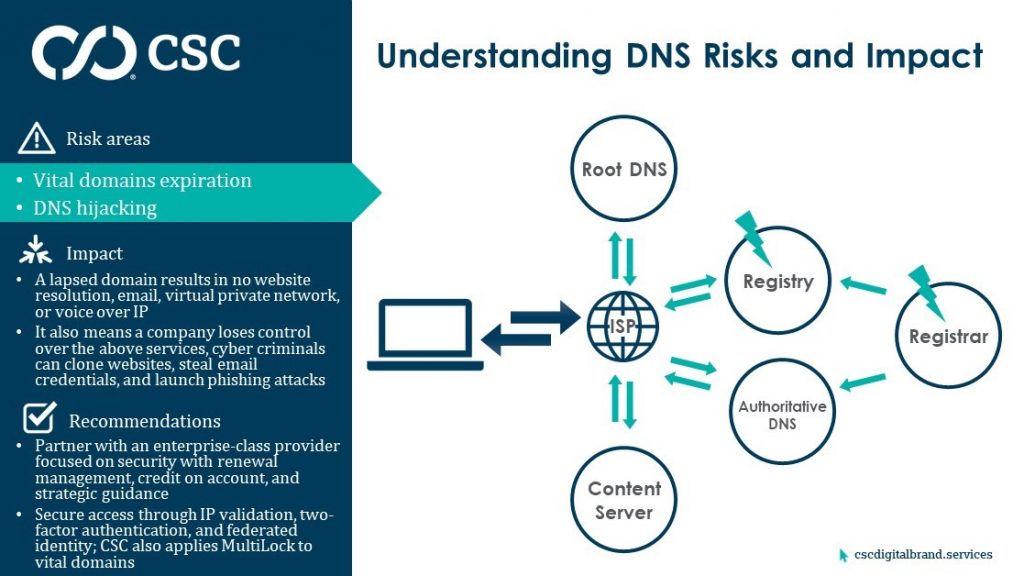
3. DNS hijacking
DNS hijacking happens at the registry and registrar level, and results in unauthorized modifications of the name servers on which a domain resides. This means the internet query responds with the illegitimate name servers of the cyber criminals instead of the company that owns the domain. DNS hijacking enables cyber criminals to redirect company website visitors to an exact replica of the brand’s site to harvest confidential information from inbound emails and launch sophisticated phishing attacks from a once-legitimate domain to gather username and password credentials.
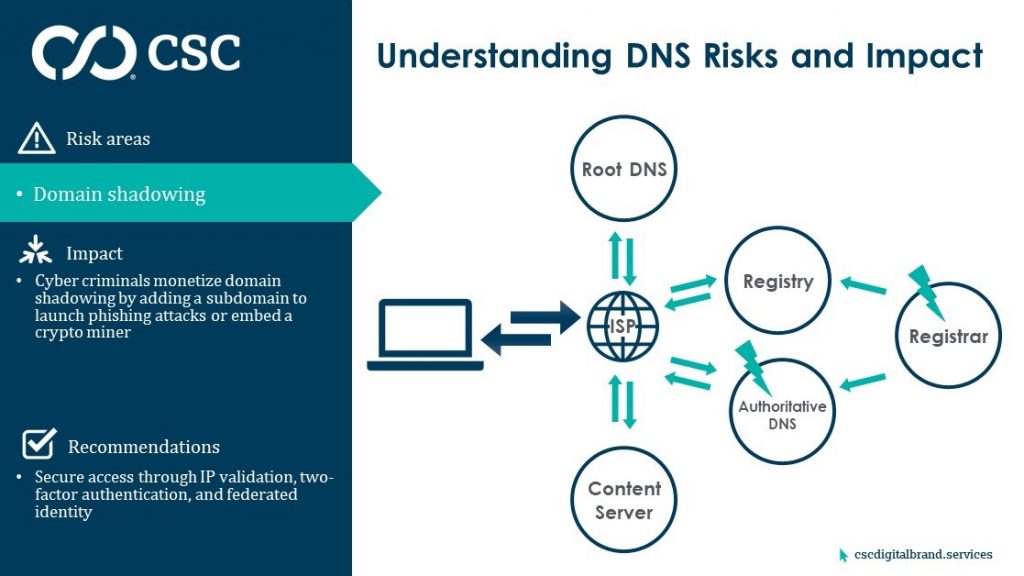
4. DNS shadowing
Just as in DNS hijacking, cyber criminals can direct company website visitors to an exact replica of the branded site to harvest confidential information from inbound emails and launch phishing attacks. Only domain shadowing is a more cunning attack, as the criminal changes the zone files of a domain instead of altering the name servers. They usually leave the website intact and add a subdomain to the zone file that can be used in a phishing attack, which is far more difficult to identify than a modification to the existing DNS or zone file.
Next post
In our next post, we’ll give you information on six more DNS vulnerabilities.
Subscribe to our blog to receive notification of new posts.
Read more posts in this series:
<< Part 1 – What DNS is and How it’s Vulnerable
>> Part 3 – Six More DNS Vulnerabilities That Make Security Crucial
>> Part 4 – The Growing Threat of DNS Hijacking and Domain Shadowing
>> Part 5 – Mitigating the Risks of 10 Serious DNS Vulnerabilities