As the war in Ukraine continues to unfold, government-led cybersecurity organizations are advising companies to strengthen their security posture, as an increase in cyber threats such as distributed denial of service (DDoS) attacks, phishing, website defacements, ransomware, and malware is likely to follow.
Observations from CSC have also shown that the general online effects of this war need to be watched as well, as some of the tactics used by fraudsters—particularly with malicious domain names and website spoofing—are magnified during a major world event. The observations below outline some of the emerging trends across a range of key online content areas and are followed by recommendations to protect against the associated threats.
Surge in domain registrations
As seen in past CSC studies, significant world events often trigger spikes in domain registrations. With the Ukraine war, we analysed the landscape based on a snapshot of all domains containing the keyword “Ukraine” that had been registered by the end of the month of the initial Russian invasion (Figure 1).

This event shows a similar pattern of activity to others that CSC has monitored, with the start of the war immediately followed by a spike in activity. Entities registering these domains—whether legitimate or with criminal intent—do so to take advantage of public interest in the emerging situation and to attract the increased web traffic.
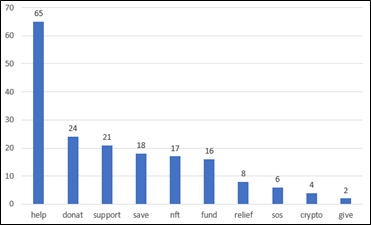
More than 700 new Ukraine-related domains were registered in the five-day period beginning February 24. These feature a range of associated keywords and content, the most potentially concerning of which are shown in Figure 2.
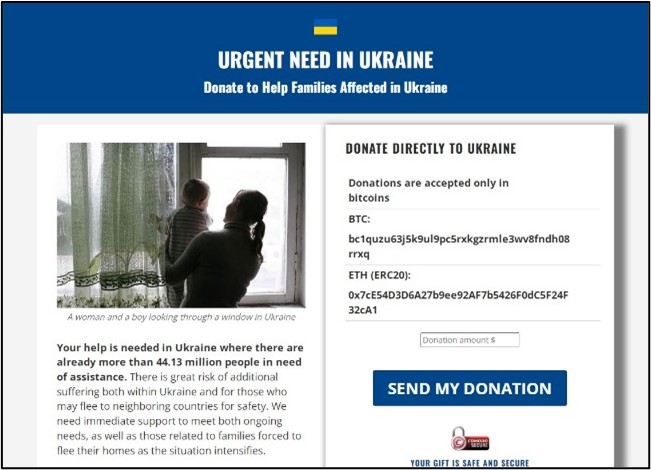
A significant proportion of the sites are directly soliciting for donations, using either traditional payment methods or cryptocurrency (Figure 3). While several may be genuine resources for supporting victims of the war, any that are not legitimate are an obvious cause for concern. They may be associated with fraudulent activity, attempting to take advantage of well-meaning people wishing to help those in need.


Many other researchers have also noted this emergence of fake donation sites, stressing the importance of contributing via legitimate agencies like the International Red Cross, Save the Children®, Doctors without Borders, or UNICEF[1],[2],[3].
Fraudulent solicitations for donations—particularly using cryptocurrency—have also been reported as circulating via numerous other routes, including phishing emails and forum posts[4]. These follow a legitimate call for donations from the Ukrainian government, posted through its official Twitter® account[5].
Interestingly, amongst the (de-duplicated) set of 170 domains featuring keywords of concern, many are registered through consumer-grade domain registrars, a trend commonly seen with non-legitimate sites.
Some of the other domains within the dataset were also found to include references to trusted charities or other key organizations, as a way of misleading internet users and adding credibility to the site content. Examples included domains with the keyword strings “redcrossukraine” (resolving to a site soliciting for cryptocurrency donations) and “nato4ukraine” (resolving to a parking page with pay-per-click links at the time of analysis).
Spread of misinformation
As with any major world event, there has been an increase in misinformation appearing online following the start of the war, which has taken several different forms.
- Recycled, out-of-context, and modified imagery – Various photos and videos purporting to show events occurring in the war in Ukraine have been circulating, particularly on social media. In many cases, these have been found to be images from unrelated events, which may have occurred many years earlier[6],[7], or are material that’s been modified[8] or falsified altogether[9]. In many cases, these posts have gone viral, with some examples attracting hundreds of thousands of views.
From a brand protection perspective, in some instances, the original sources of the material can be identified through open-source investigation techniques (e.g., reverse-image searches). Similar approaches may be possible using screen grabs taken from video content. Furthermore, geolocation techniques can sometimes be used to verify the geographical origin of imagery[10].
General advice for internet users is to be mindful of the origins of information, and only to share content from trusted sources.
- Pro-Russian content and propaganda – We found significant amounts of online content showing support for Russia. While some of this will presumably be legitimate, a significant amount (particularly on social media) appears to have been posted by Russian state-sponsored profiles or automated accounts (bots). Recent creation dates, low numbers of followers, and high numbers of likes for postings, are characteristics that demonstrate profiles may fall into this latter category. Social media is a popular channel for spreading propaganda and generating political support due to the ease of creating content, combined with its wide potential reach and speed of spread (Figure 4). Many of the identified postings make use of popular hashtags (e.g., #istandwithrussia or #istandwithputin), or associate their content with other emotive issues (e.g., Israeli or Palestinian content). One study[11] found that a significant subset of these postings were intended simply to attract traffic, in some cases driving readers to eCommerce listings or websites for other service providers.
Another significant observation is that even some mainstream Russian-based news accounts have been suspended from social media platforms in response to their pro-Russian stance and justification of military action based on reasoning unsupported by the known facts[12],[13]. Meta (the organization behind Facebook®, Instagram, and WhatsApp) announced its refusal to cease fact-checking content posted by Russian state-owned media[14], as demanded by Russian authorities. Furthermore, on March 6, TikTok announced that it was suspending the creation of new videos in Russia. This was due to uncertainty around the safety of content creators following the introduction of Russia’s fake news law, which can impose up to 15 years’ imprisonment on those found publicly calling for sanctions, or spreading what Russia perceives to be false information about its military[15].
- Conspiracy theories and other fake information – One of the common themes identified in online commentary, particularly on social media, are claims that the war is fake[16]. In some cases, this has been accompanied with claims that real imagery has been staged[17]. These claims have been made by a range of entities, typically promoting pro-Russian or conspiracy theorist agendas.
An additional concerning observation is the use of fake accounts to post fake messages, such as the case of a Telegram account purporting to be that of Ukrainian President Volodymyr Zelenskyy[18]. Several outlets claiming to offer breaking news stories have been circulating fake news, with the content on these untrustworthy channels frequently unaccompanied by sources or any other evidence[19].
Direct effects on online businesses and organizations
The war in Ukraine has had a range of effects on corporations, from the Russian authorities blocking internet access to several key western websites and platforms (particularly social media), to organizations withdrawing business operations in Russia. Conversely, there’s also been a rise in activism against corporations who have failed to pull out of Russia, with hashtags such as #boycottcocacola and #boycottmcdonalds trending on social media in the first two weeks following the invasion.
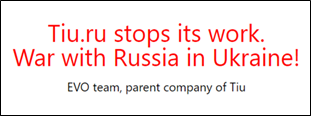
A particularly significant effect from a brand protection point of view is the direct repercussions for both Ukrainian and Russian online organizations resulting from the business interruptions, sanctions, and economic damage that have arisen during the war. One example is the closure of a series of Ukraine-based websites and marketplaces. One affected organization is EVO (evo.company), the Ukrainian IT company behind a range of eCommerce platforms in the region, including Prom.ua, Tiu.ru, Bigl.ua, Deal.by, and Satu.kz, among others. At the start of March, the Tiu.ru website suspended its operations in response to the war (Figure 6). This website was tailored to the Russian market but had been hosted on Ukrainian servers[20].
These changes will have a domino effect on the eCommerce landscape in the region, the balance of available legitimate and counterfeit products, and may ultimately lead to the emergence of new marketplace sites to take their place.
Conclusion and recommendations The Ukraine war increases the possibility of cyberattacks against Western websites and internet infrastructure. Employing a robust domain security posture is critical. In times of global uncertainty, companies should not only have advanced security measures in place to safely mitigate threats, but should also employ a holistic online monitoring program to ensure rapid detection and allow for quick and effective takedown of any IP abuse, such as fake sites, fraudulent campaigns, or other false content or misinformation.
CSC recommends taking the following steps.
- Confirm that your domain registrar’s business practices are not contributing to fraud and brand abuse. The following issues are often common with consumer-grade domain registrars:
- Operating domain marketplaces that drop catch, auction, and sell domain names containing trademarks to the highest bidder
- Domain name spinning and advocating the registration of domain names containing trademarks
- Monetizing domain names containing trademarks with pay-per-click sites
- Experiencing frequently occurring breaches resulting in DNS attacks, phishing, and business email compromise
- Identify trademark and copyright abuse in web content, and on online marketplaces, social media, and mobile app stores via an online monitoring service.
- Leverage global enforcement, including takedowns and advanced techniques in internet blocking.
- Employ phishing monitoring and a fraud-blocking network of browsers, partners, internet service providers (ISPs), and security information and event management (SIEM) systems.
We’re currently engaged with many of our customers to both assess and provide tangible recommendations to quickly control threats. If you have any questions on developing your own cybersecurity checklist, please contact us.
[1] domaingang.com/domain-news/new-help-ukraine-domains-are-most-likely-not-legit/
[2] welivesecurity.com/2022/02/27/beware-charity-scams-exploiting-war-ukraine/
[3] twitter.com/ESETresearch/status/1497194165561659394
[4] bleepingcomputer.com/news/security/help-ukraine-crypto-scams-emerge-as-ukraine-raises-over-37-million/
[5] twitter.com/Ukraine/status/1497594592438497282
[7] bbc-monitoring.co.uk/campaign/RwbbAiso/aab564822c8140a6c46681ea/b680b576f310643c916458a491cf5d77
[8] twitter.com/Shayan86/status/1496944075378855942
[9] cnn.com/2022/03/05/politics/fact-check-fake-cnn-ukraine/index.html
[10] youtube.com/watch?v=KtOaC0emsxY
[11] twitter.com/marcowenjones/status/1499312091727020032
[12] euronews.com/next/2022/03/02/ukraine-war-facebook-and-youtube-block-russia-s-rt-and-sputnik-in-europe
[13] businessinsider.com/facebook-ukraine-russia-news-state-media-2022-3
[14] twitter.com/nickclegg/status/1497279120853590025
[15] theverge.com/2022/3/6/22964418/tiktok-suspends-creation-new-video-content-russia-ukraine
[17] twitter.com/hoaxeye/status/1497514958174699522
[18] twitter.com/Shayan86/status/1497485340738785283