
By Vincent D’Angelo, global director
Share this post



As outlined in CSC’s recent 2020 Domain Security Report: Forbes Global 2000 Companies, cyber criminals are disrupting organizations by attacking the protocol responsible for their online presence—their domain name system (DNS). When a DNS is overwhelmed with traffic due to a distributed denial of service (DDoS) attack or configuration error, content and applications become inaccessible to users, affecting both revenue and reputation. The estimated cost of a downtime can exceed $500,000 an hour.
Over the years, there have been several incidents that have caused significant DNS disruption—most recently due to the COVID-19 global pandemic. According to the latest Kaspersky report, DDoS attacks are up 217% in comparison to the second quarter last year, and up 30% from first quarter of 2020. Many of these disruptions could have been mitigated with an effective DNS redundancy program. A secondary DNS can effectively split your DNS traffic between two trusted networks that not only prevents your brand against a single, takedown DDoS attack, but also improves your DNS redundancy.
Following the same methodology outlined in our Domain Security report, our research looked into DNS redundancy and found some startling findings:
- Only 19% of the Forbes 2000 are using some sort of secondary DNS (or redundancy)
- Only 20% utilize enterprise-grade DNS
In 2018, the Harvard Business School (HBS) published a paper—“Evidence of Decreasing Internet Entropy: The Lack of Redundancy in DNS Resolution by Major Websites and Services”—where they explored how the tendency not to deploy multiple DNS providers could cause issues. Many organizations have clearly not made the necessary changes for secure against this risk.
The concept of DNS redundancy and diversification have been promoted as a best practice as early as 1997. However, the resistance to adopt this practice can be attributed to “[the] cost, difficulty, and potential technical issues associated with diversification among multiple providers.” In addition, the service model of some providers does not allow for domains to register a secondary nameserver managed by a different DNS provider.
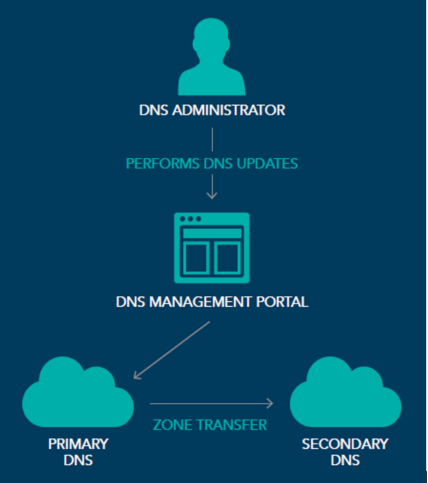
How primary and secondary DNS works
1. DNS administrator logs into DNS management portal
2. DNS administrator updates a DNS record
3. Change propagates through DNS network
Having the DNS split between multiple services, ensures that websites, apps, and other online assets would be less likely to have gone down—even during the height of the attack. Companies should be prudent and not wait for another incident and succumb to an attack themselves or on their providers before considering the use of a secondary DNS service.